Censorship and Surveillance in the Digital Age: Part One
A multi-part series on methods of censorship and surveillance, why they matter, and how to circumvent them.
Photo by Max van den Oetelaar on Unsplash
Part One
Introduction
The age of the internet has brought with it access to seemingly unlimited information. What happens, though, when a government decides to limit the information that its citizens have free access to, or uses the internet as a tool of surveillance against its own people? In 2021, the southeast Asian country of Myanmar, with a population of 55 million, suffered a military coup. Leaders and other influential people were imprisoned. The new government declared a state of emergency, and right away, internet restrictions were put in place so that the citizens would not be able to organize protests or access news. ISPs and telecom providers were forced to install spyware that could track people and monitor communications. Social media sites were blocked as well. This series of events is a perfect example of what a determined government can do to prevent citizens from being informed and from being able to communicate with each other and with the outside world.
In China the “Great Firewall” limits internet sites that Chinese citizens can access and allows the government to monitor everything they do online (see "Case Study: The Great Firewall of China" below). Russia isn’t far behind, criminalizing tools such as VPN’s that allow internet users to remain anonymous and access information blocked in certain regions. Other countries notorious for censoring the internet and engaging in mass surveillance include North Korea, Iran, Iraq, Turkmenistan, Pakistan, Egypt, Saudi Arabia, and the UAE. In Germany and other European countries, speech online is curtailed by laws criminalizing insulting speech and malicious gossip. Could it happen here in the United States? Edward Snowden showed us the extent to which our government had gone to monitor its citizens, and how advanced the surveillance technology had become (and that was over a decade ago). The Patriot Act, put in place after the attacks of 9/11, allows mass surveillance of American citizens to take place. More recently, threats by politicians against news agencies suggest a willingness to weaponize the resources of the government against free speech, while other politicians have pushed for the regulation and censoring of "misinformation" and "disinformation" on social media sites.
How Do Computers Communicate?
A discussion of online censorship and surveillance has to start with a discussion of how computers actually communicate. When computers need to "talk" to each other, whether it's a conversation between two computers on a network or between a computer and a website server, they do so by sending packets of information back and forth. The packets contain information on the source and destination as well as the information to be transferred. So, if your laptop to needs to communicate with a website, it sends a request to communicate, the server then acknowledges the receipt of the packet (it is a little more complicated than that, but this is basically what happens), and then they can begin a session.
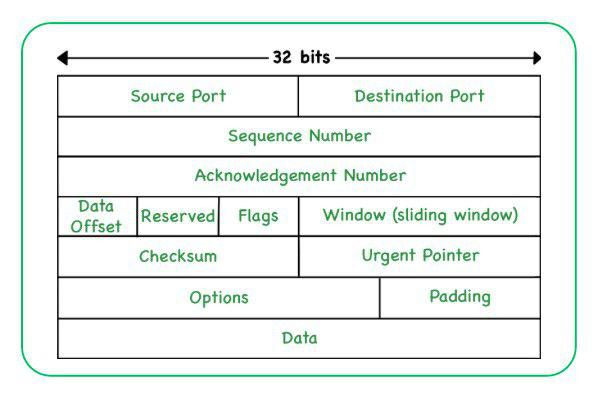
A diagram from geeksforgeeks showing all the information contained in a TCP packet:
The two computers need to be able to recognize each other. So, every computer has what is called an IP Address. That address is assigned either by a router (via what is known as DHCP), or by an ISP or network administrator. The IP Address of both computers is included in the packet so that the packet is routed correctly. IP addresses come in two types. IPV4, which is the form most people recognize, might look like 192.168.10.1. (a 32 bit number). When it became obvious that the internet was too big for 32 bit numbers (there weren't going to be enough of them), a second type, IPV6, was developed. It is a 64 bit number and looks more like 2345:0425:2CA1:0000:0000:0567:5673:23b5.
As noted above, IP Addresses are assigned to a computer by one of a few different methods, but it's actually a bit more complicated than that. Your router assigns all computers in your home or office an IP Address via it's DHCP server. These are not the addresses that the internet sees. Your router has an "external facing" IP Address, usually assigned by your ISP. This makes your home network more secure.
If we only had IP Addresses, every time an internet user wanted to access a website, they would have to remember and type in the IP Address. Fortunately, that's not necessary because of DNS (Domain Name System). DNS converts IP Addresses to names like google.com, making web surfing easier. DNS is usually provided by ISPs, but there are alternative sources (discussed in Part Two).
The last set of terms relate to packets. Packets are transmitted using one of two protocols. The protocol is attached as a packet "header." The first, TCP or Transmission Control Protocol, is used for any type of connection where dropped packets can interfere with the integrity of the data. The other, UDP, or User Datagram Protocol, is used for transmission of data where some dropped packets are less important than speed, such as in video calls.
Methods of Internet Censorship
If a government, nation-state, or other entity wants to limit the flow of information, there are multiple options they can choose from. It is possible to block the IP Address of a website so that it can't be accessed. If someone tries to view the site, the request is dropped. Alternatively, it is possible to redirect their request to a null site so it looks as if the site is simply unreachable. The typical method used for IP blocking is to create a list of blacklisted addresses. When someone tries to access one of these addresses, a surveillance computer blocks the request. China uses huge servers that send reset requests whenever a login or request sent to a restricted site is intercepted, causing the connection to be terminated. A downside of this technique is that sometimes multiple websites may be linked through a common server, so ALL of them may be blocked.
Related to this is DNS blocking. DNS is the beginning step for accessing a website, so DNS blocking is a common censorship method. There are a few different ways this can be done. A DNS server can be configured to block a DNS address, or a fake address can be provided, redirecting the request to another site. This is known as DNS tampering or DNS poisoning. There are alternative DNS servers such as google (8.8.8.8) and Cloudflare (1.1.1.1), and governments could block these third-party DNS providers as well as the default servers.
Another method of censorship, network throttling, occurs when an ISP or nation-state deliberately slows internet traffic, either in general or to specific sites. Note that internet slowdowns aren't always intentional or malicious. They could just be due to poor connectivity or infrastructure problems. Also, in areas where bandwidth is at a premium, access to resource intensive sites might be limited to preserve general access by the population. When it is done to limit the free flow of information, though, it becomes censorship. According to the Advocacy Academy, this method was used in Russia in 2021 to limit access to Twitter after the social media giant refused delete material the Russian government objected to.
It is also possible to block TCP connections to certain sites, known as TCP blocking. This prevents what is known as the TCP Handshake, which is how two computers connect via TCP. The ports that are used for connections can also be blocked. Port 443 is used for HTTPS connections (HTTPS is the method used for encrypted TCP connections). If port 443 were blocked, only unencrypted connections would be allowed. If port 80 (HTTP) and port 443 were blocked, no connection would be possible.
Finally, there is deep packet inspection or DPI. This is a sophisticated method of blocking where the entire packet is analyzed. DPI looks for keywords, encryption protocols, and other signatures. It can detect and block VPN traffic as well as HTTPS. It also a very fine-grained form of control. DPI can use keywords to block certain parts of a website pages but not the entire site. This gives a government very tight control over what their population can see. According to Advocacy Academy, the market for these products is expected to reach $4 Billion in 2025. Once again, the Chinese government is notorious for using DPI as part of their "Great Firewall." DPI does have legitimate uses, such as when it is used in intrusion detection systems (IDS) in cybersecurity.
Other methods of censorship include URL blocking, where certain URLs are blacklisted, site blocking, where certain sites are blocked, and domain deregistering. Of course, a government should just shut the internet down altogether, or use coercion and intimidation to scare people into compliance.
Detecting Internet Shutdowns and Slowdowns
Detecting internet shutdowns and slowdowns, and differentiating them from normal outages that occur regularly all over the world, isn't straightforward. Fortunately, there are tools that can help. Researchers at Georgia Tech's Internet Intelligence Lab have developed an online tool called Internet Outage Detection and Analysis (IODA) which can be found at
https://ioda.inetintel.cc.gatech.edu/
This tool allow searches for outages worldwide or by region. They use three different indicators to determine connectivity and to attempt to differentiate between those that are accidental and those that are intentional. Here is a screenshot showing all countries:
By clicking on a country, different measured parameters can be viewed:
It's worth paying particular attention to the BGP parameter. BGP stands for Border Gateway Protocol, and is how different internet regions stay connected. BGP routers make sure that internet traffic is directed to the appropriate regional network. BGP is a stable signal most of the time, so a drop off is likely to indicate a significant disruption. In the above graph, BGP (in green) is stable, so this is more likely an unintentional outage in the United Kingdom.
Another useful tool is the Open Observatory Of Network Interference (OONI) probe. The OONI probe runs on most platforms and also has iOS and Android apps. OONI runs probes for the following parameters:
Blocking of websites
Blocking of instant messaging apps
Blocking of censorship circumvention tools
Speed and performance
Middleboxes in the network
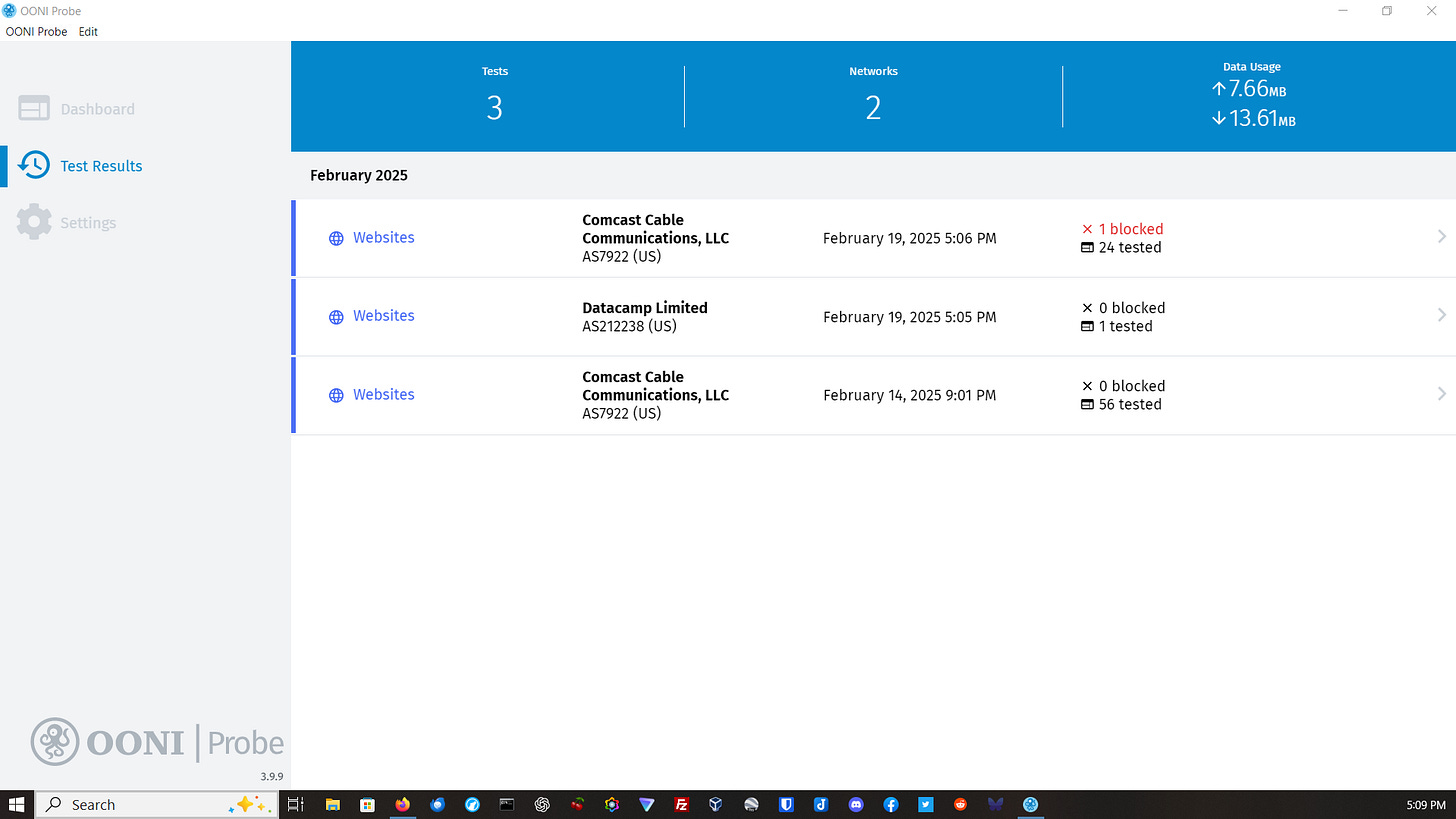
Here is a probe of an ISP, looking for blocked websites:
The result showed one site is blocked:
Clicking on a result gives more information about blocked sites. In this case, It is likely that this site was blocked because of a risk of illegal content or malware. If this were a site blocked by a government or nation-state, and a dissident, journalist, or regular citizen needed to access it, censorship circumvention tools would be needed to do so.
Online Surveillance
Surveillance is another issue altogether. Most people are familiar with the ubiquitous cameras that seem to be popping up everywhere, and they've heard about technology like facial recognition that can pick someone out of a large crowd. What about surveillance of online activities, though? The average person most likely assumes that if they are not breaking the law, they don’t need to care about online privacy. What happens, though, when a government decides to block access to what is going on in the country or in the outside world? What happens when an internet user can get arrested (or worse) for sending or receiving information? Dissidents and journalists around the world have to play a cat and mouse game to avoid arrest or even death while trying to ensure the free flow of information.
It is difficult to even list all the ways a person can be tracked and monitored online. Obviously, an ISP can keep a record of all the websites they’ve visited. They can then sell this information to marketers or other entities. In reality, pretty much everything a person does online is tracked. Online behavior is tracked and analyzed by websites and marketers via internet tracking, also known as browser tracking, data tracking, or web tracking. The best known method is via cookies. Cookies store information about users on websites so that the website can provide better and faster service when the site is visited again. Some cookies, known as third-party cookies, store information about users on other sites.
Browser Fingerprinting
Browser fingerprinting is a particularly insidious and hard to detect form of tracking. It relies on piecing together information about a person's browser and device so that their browsing activity can be followed. A browser is fingerprinted easily, giving interested parties access to browsing habits. Evelyn Chea explains browser fingerprinting in her blog:
"Browser fingerprinting is a set of tools and techniques that can capture data through a web user's browsing activity. Browser fingerprinting gathers information related to a user's operating system, browser type, screen resolution, time zone, keyboard layout, and more. By processing these details, it creates a unique identifier, or "digital fingerprint," for each user. This identifier remains consistent across different browsing sessions, making it a reliable tool for visitor identification beyond the realm of traditional cookies."
Browser fingerprinting does serve useful purposes. It is used by websites and financial institutions to prevent fraud, protect against botnet attacks, and to provide targeted advertising. Unfortunately, it can also be a reliable method of identifying and tracking users.
Norton identifies eight other methods used to track internet activities:
Account Tracking - What are you logged onto?
Web Beacons - How you interact with a web page
Mouse Tracking - Records your mouse/cursor movements
IP Addresses - Remembers your IP Address
Favicons - "Supercookies" that are difficult to remove
Session replay scripts - Record mouse movements, clicks, and scrolling
Cross-device tracking - matches browsing across devices
Click-through-rate - How often you revisit content
Companies like Google, Microsoft, and Facebook also store huge amounts of data about internet users. Microsoft 10 and 11 both send data about everything a person does on their computer back to Microsoft. That doesn't actually mean that your data is at risk, but they can be coerced to turn this information over to a government agency. Right now, it (probably) requires a warrant, but that could change. They know email addresses, phone numbers, search histories, passwords, health issues, etc. When a person visits a website, cookies are placed on their computer. They can then be tracked using these tracking cookies.
Surveillance on SMS and Email
Surveillance is also an issue on SMS, phone, and email. Many SMS services claim to use encryption, but users usually have to opt in. Telegram is an example of a messaging service that requires opting in to have end-to-end encryption. Some, like Apple Messages, use end-to-end encryption, but they can still store user data. Most texting services have vulnerabilities that make them insecure for sensitive messaging. Email has the same issues. Unencrypted email can be intercepted fairly easily. Even encrypted email stored on a server at Google, Yahoo, or other providers could be accessed by the government or hackers.
At the most advanced level, malware can be placed directly on a cell phone to monitor all communications. In 2021, Apple notified iPhone users they believed were targeted by spyware created by the Israeli company NSO group. Analysis by Citizen Labs found that the phones of 30 Thai pro-democracy advocates were infected with Pegasus spyware. Pegasus is a tool that can be placed on an iPhone via what is known as SMishing. It was designed for legal use by governments but rapidly became a tool for oppressive regimes to use to monitor dissidents and journalists. According to Citizen Labs:
We have identified at least 30 Pegasus victims among key civil society groups in Thailand, including activists, academics, lawyers, and NGO workers. The infections occurred from October 2020 to November 2021, coinciding with a period of widespread pro-democracy protests, and predominantly targeted key figures in the pro-democracy movement. In numerous cases, multiple members of movements or organizations were infected.
Many of the victims included in this report have been repeatedly detained, arrested, and imprisoned for their political activities or criticism of the government. Many of the victims have also been the subject of lèse-majesté prosecutions by the Thai government.
Pegasus spyware is also believed to have been used to monitor the family and associates of Jamal Khashoggi, a Saudi journalist who was brutally murdered by Saudi operatives in 2018. Saudi Arabia is a known client of the NSO Group.
Data At Risk
Obviously, not all collected data is going to a government or nation-state, but it certainly means that there is a lot of information about citizens' computer use and browsing habits being monitored and stored. It all begs the question, though: how much can they collect. In 2013, The Guardian and The Washington Post published documents provided by ex-NSA contractor Edward Snowden. These leaks show that the National Security Agency (NSA) in the United States and the Government Communications Headquarters (GCHQ) in the United Kingdom are capable of massive surveillance of ordinary citizens. For example, X-Keyscore was a tool that allowed the NSA to track any internet user's online activity. According to Bill Mann at blokt.com:
[X-Keyscore] is perhaps the most powerful NSA internet espionage tool of them all. Also known as XKS, this computer system is designed to search through and analyze internet data from users all over the globe, and huge amounts of that data are being collected each and every day.
What’s more, all of that data can then be shared with other intelligence agencies as part of the ‘Five Eyes‘ and ‘Fourteen Eyes’ alliances, so agencies like the GCHQ in the United Kingdom or the Defense Intelligence Headquarters of Japan could also get access to information on a person’s browsing habits, search history, and general internet usage.
Case Study: The Great Firewall of China
In the 1990's, faced with the question of how to maintain societal cohesion and how to restrict the flow of information that might be counter to their interests, the Chinese government began to build what would be come to be known as "The Great Firewall of China." Officially called the Golden Shield Project, the Great Firewall would grow to become a tool for massive content filtering and blocking. In 2025, it is arguably the most sophisticated effort of its kind in the world, and is an excellent case study because it utilizes so many different censorship and surveillance technologies.
The Great Firewall can intercept information going either into or out of China. All of the data passes through network gateways where it is analyzed and, based on constantly updated criteria, is either allowed to pass through or is blocked or diverted. The Chinese government does not do this alone; Chinese internet service providers (ISPs) are required by law to participate, and can suffer fines and other consequences for failing to comply.
The ISPs install software designed to filter content before it can reach internet users. They are subjected to audits to be sure they are in compliance, and are required to update filtering methods as required. At the gateways themselves, multiple technologies are employed. DNS poisoning, usually the first level of control, sends requests to alternative addresses. IP blocking is also employed. Many sites available to most of the rest of the world are blocked. If If a gateway receives a request from a user for one of these sites, the connection is dropped. Blocked sites include:
Facebook
Twitter
Google
YouTube
Linkedin
BBC News
Instagram
Wikipedia entries not approved by censors
Many other news and social media sites
At the next level of sophistication, the Great Firewall utilizes complex algorithms to filter keywords. The algorithms are sensitive enough to filter words as well as phrases, preventing internet users from being able to engage in undesirable conversations. Keyword filtering is an imperfect tool, but the Great Firewall has other technologies that can be brought to bear. Deep packet inspection allows authorities to analyze entire web packets, including origin, destination, and the data in the packet. These sophisticated methods can be done in real time, so internet users' requests are blocked or redirected before undesirable content can be viewed or shared.
The Great Firewall seems to having the desired affect, especially among young people. Where once this segment of the population would protest against or try to circumvent the censorship methods used by the Chinese government, now they are more likely to ridicule those expressing undesirable opinions. According to Human Rights Watch:
For many years, the internet in China was seen as a channel for new thinking, or at least greater openness; Chinese citizens could go online to expose government corruption and criticize leaders. Online discussions were relatively free and open, and users, especially younger ones, had an eager appetite for learning and debating big ideas about political systems and how China should be governed.
That has changed sharply in recent years as a crackdown on the internet and civil society has become more thorough and sophisticated—and the government’s messaging has grown more nationalistic.
That nationalistic messaging now seems to resonate with young Chinese who have been continuously exposed only to messaging deemed appropriate by Chinese authorities.
Part 2 of this series will discuss methods to circumvent online censorship and surveillance.
Sources:
https://www.advocacyacademy.org/
https://www.accessnow.org/russia-throttled-twitter/
https://switchvpn.net/blog/what-is-internet-surveillance-and-ways-to-avoid-it/
https://fingerprint.com/blog/browser-fingerprinting-techniques/
https://www.futurescope.co/how-chinas-great-firewall-works/
https://www.hrw.org/news/2020/09/01/china-great-firewall-changing-generation